If you’re building and managing applications in public cloud providers like GCP or AWS, chances are you’ve heard of VPC peering. This blog post explains what VPC peering is, why you’d want to use it, and, if you’re using CockroachDB Dedicated today, how you can get started with our VPC peering functionality.
What is a VPC and what is VPC peering?
A virtual private cloud (VPC) is a logically isolated, virtual network within a cloud provider. A VPC peering connection is a networking connection between two VPCs that enables you to route traffic between them using private IP addresses. VPC peering allows you to deploy cloud resources in a virtual network that you have defined. Instances in either VPC can communicate with each other as if they were within the same network. Data can be transferred across these resources with more security.
What are the benefits of using VPC peering?
Improve security. VPC peering comes with the major benefit of improving security by enabling private connectivity between two or more VPC networks, isolating traffic from the public Internet. Because your traffic never leaves the cloud provider’s network, you reduce a whole class of risks for your stack.
Save money on network costs. With VPC peering, you save on network transit costs and benefit from improved network latency. Because peering traffic does not leave your cloud provider’s network, that reduces public IP latency. And since peered networks use internal IPs to communicate, transferring data over the cloud provider’s network is cheaper than over the public Internet.
Get more flexibility for services that don’t need to connect to the Internet. Another reason to use VPC peering is when your instances do not require a public IP address or a network address translation (NAT) configuration to the public Internet. This can be desirable for backend services, where a user wants to block all egress traffic to the public Internet from their instances.
VPC peering in CockroachDB Dedicated
CockroachDB Dedicated, our database-as-a-service, provides you with the ability to set up VPC peering to directly peer your GCP VPCs with your CockroachDB Dedicated cluster’s VPC. Or, if you use AWS, you can set up a PrivateLink connection to securely connect your AWS VPCs with your CockroachDB Dedicated cluster.
Before, CockroachDB Dedicated required you to authorize networks that could access the cluster, typically including your application server’s network in a production environment, as well as your local machine’s network in a development environment. This process was clunky and also had some limitations when running applications in Kubernetes.
Now, VPC peering and AWS PrivateLink gives you a faster and smoother user experience. You can sidestep the old requirement of allowlisting IP addresses within CockroachDB Dedicated before you’re able to connect (though that IP allowlist option is always available if the need arises).
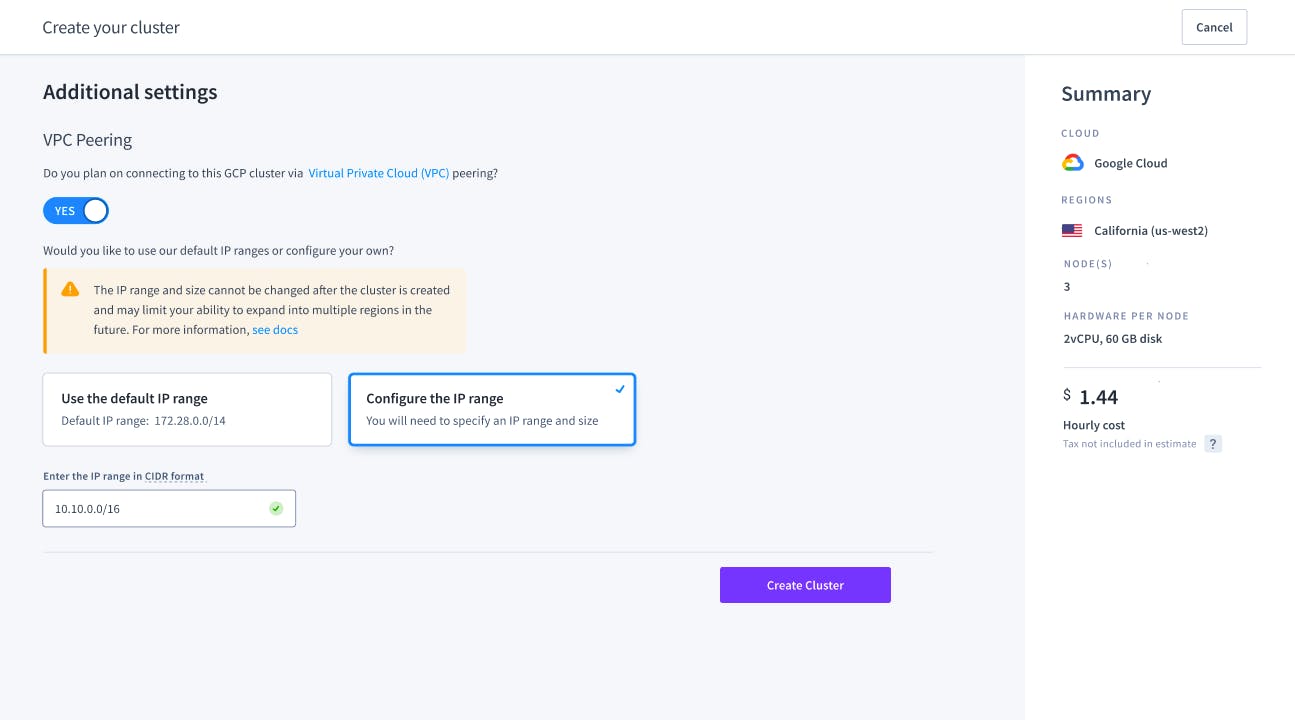
How to set up VPC peering in GCP in 3 steps
1. At the moment of creating a cluster, you can specify an IP address range (in CIDR notation) for your CockroachDB Dedicated cluster’s network. That range should not overlap with the IP ranges in your application’s network.
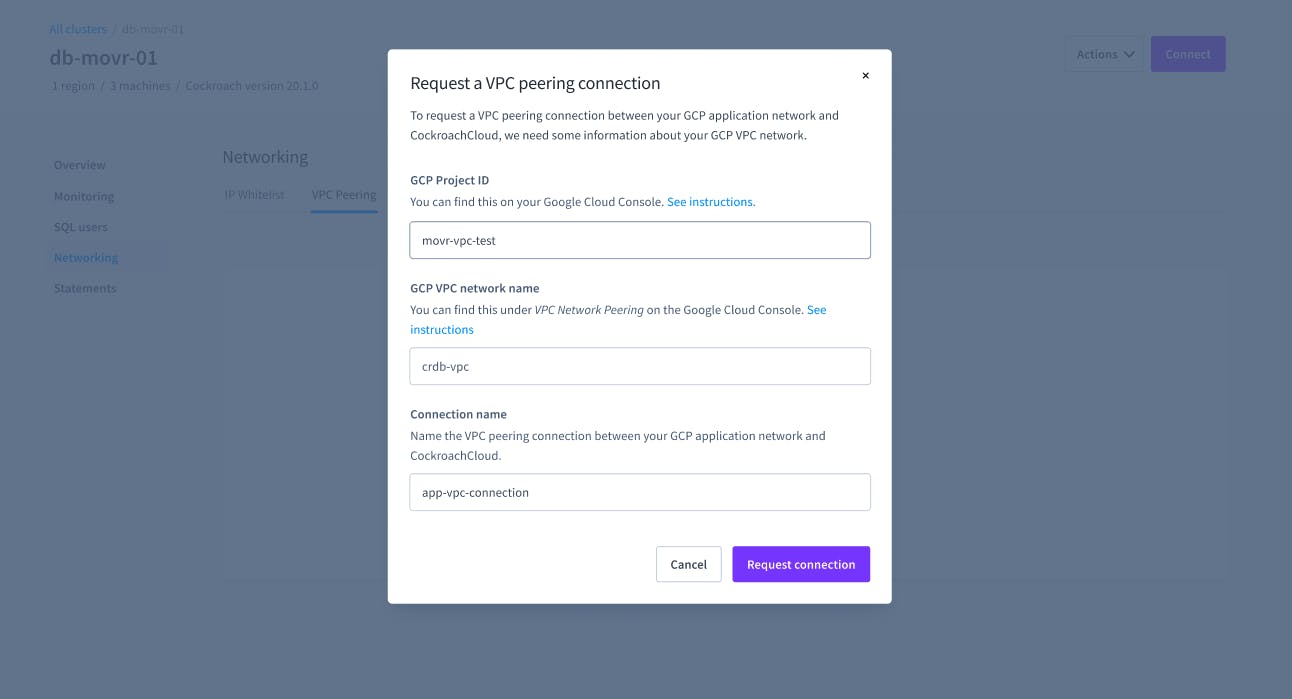
2. Once your cluster is configured, you kickoff the VPC peering request by adding your GCP project ID and GCP VPC network name.
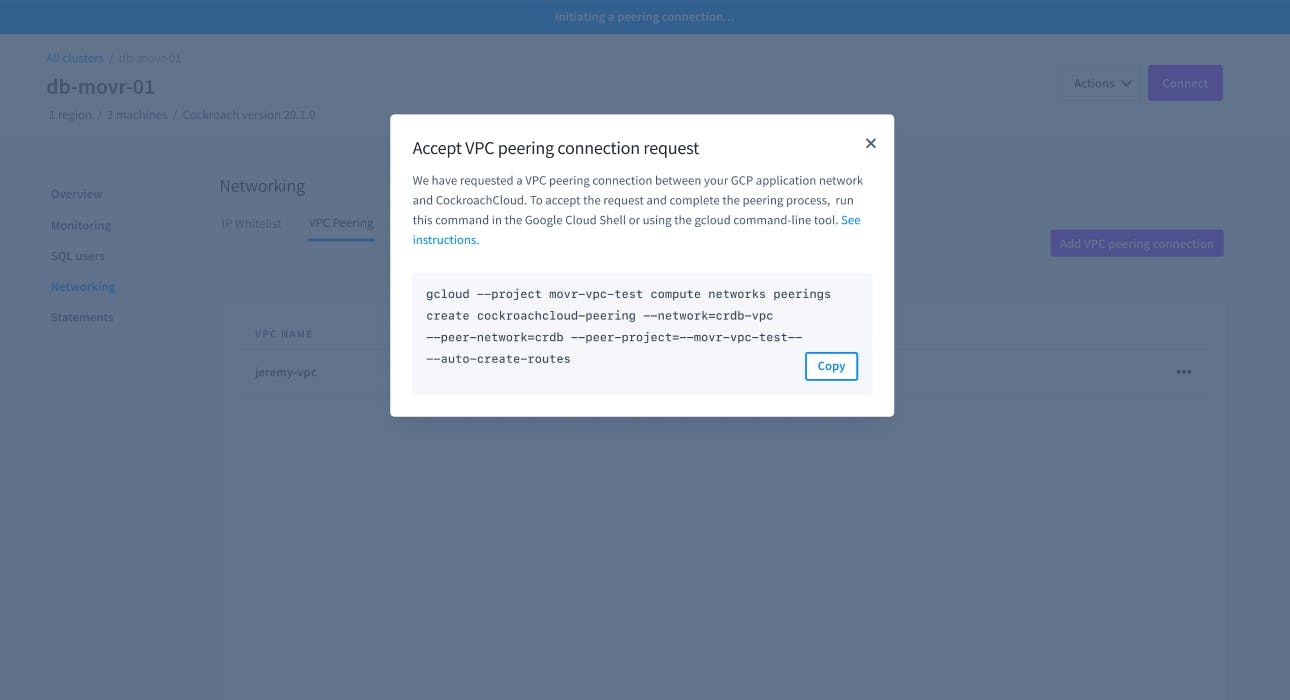
3. CockroachDB Dedicated will provide you a handy gcloud command line to run which will allow GCP to accept the new VPC peering request.
How to set up AWS PrivateLink
If you’re using AWS, you can securely connect AWS VPCs with CockroachDB Dedicated with AWS PrivateLink.
Step One: PrivateLink Connection
After creating your cluster, you can start to set up a PrivateLink connection by visiting the Networking page.
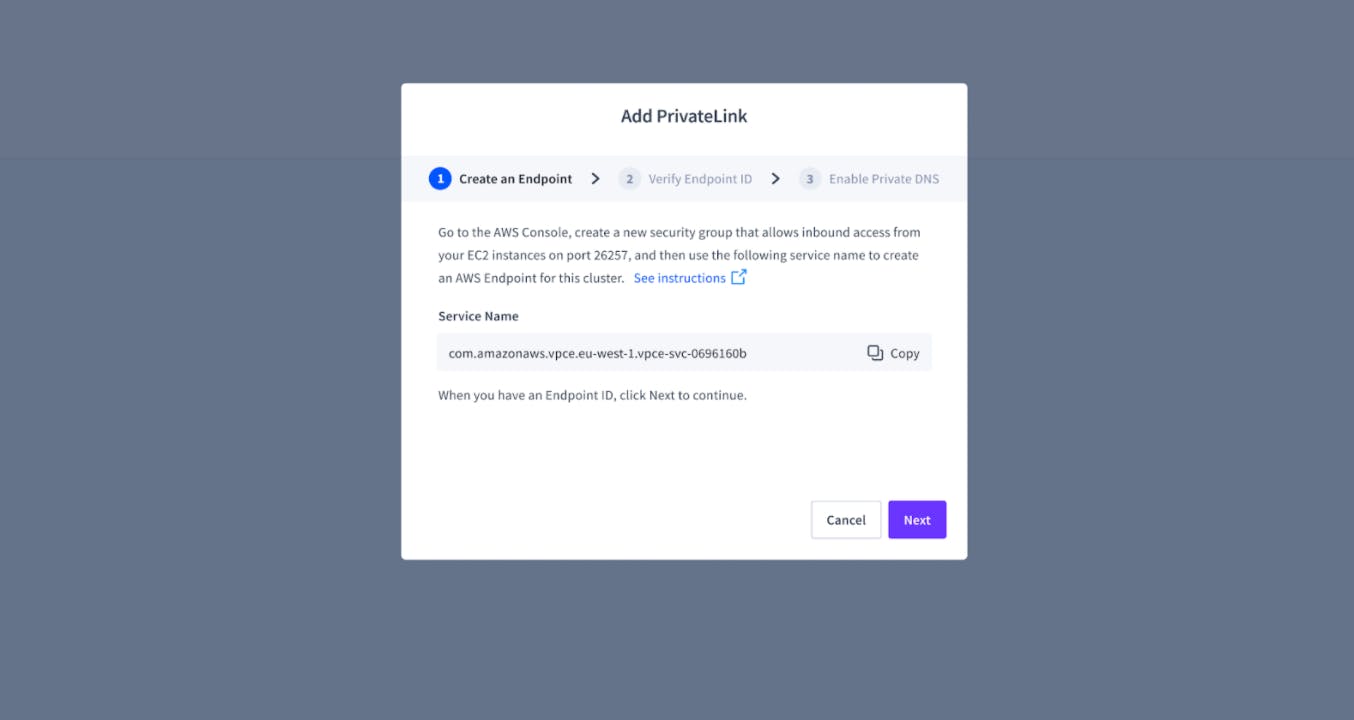
Step Two: AWS Endpoint
Start by creating an AWS endpoint and pasting that ID into the modal. We provide instructions on how to do so through the Amazon VPC Console.
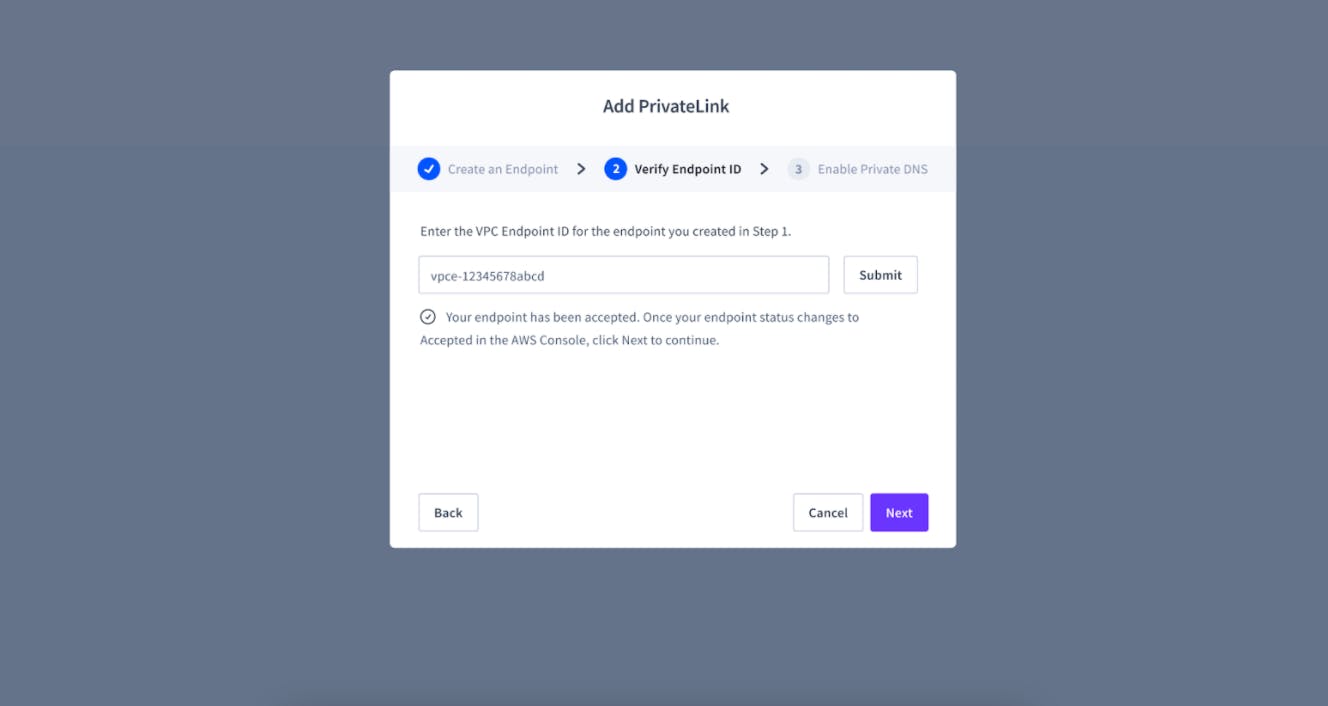
Step Three: Verify VPC Endpoint ID
Verify the VPC endpoint ID to allow CockroachDB to accept the endpoint request.
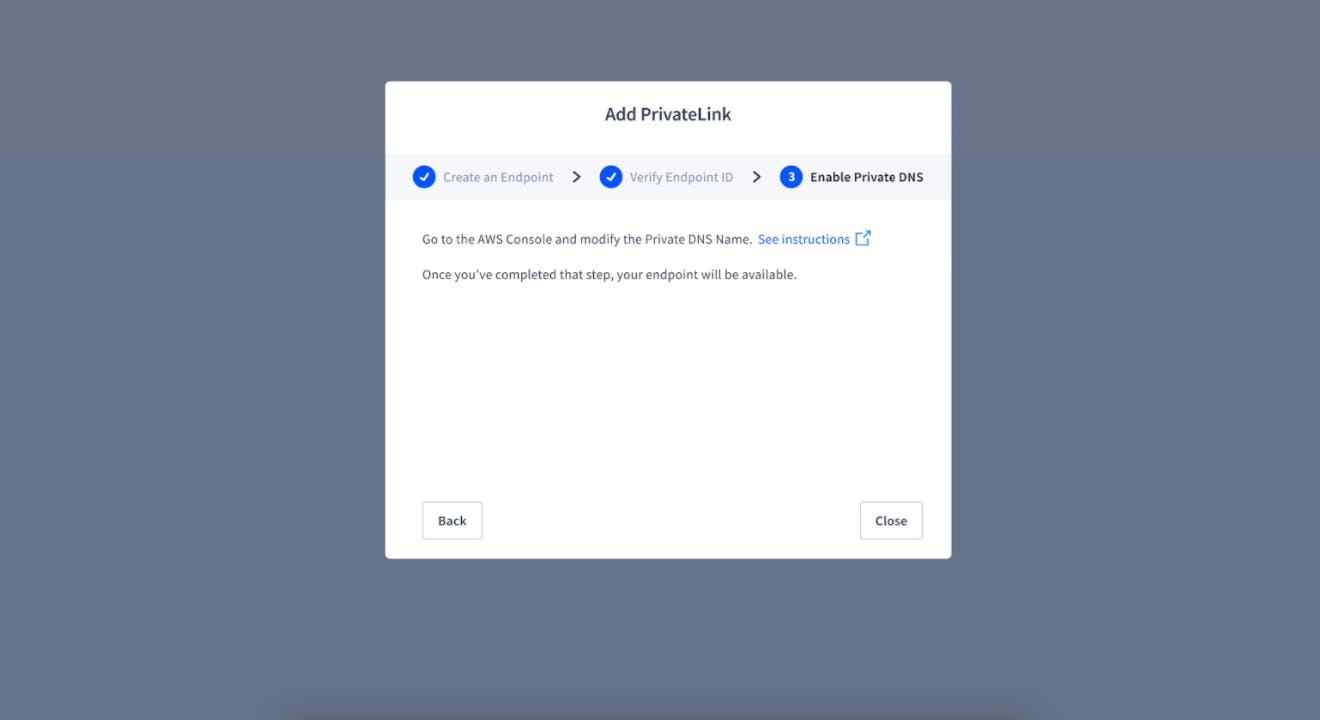
Step Four: Enable Private DNS
After request acceptance, we provide instructions on how to enable private DNS. Once this is complete, you can connect to your cluster using PrivateLink.
Learn more about VPC peering in CockroachDB Dedicated
With VPC peering and AWS PrivateLink, you can securely connect your applications with your CockroachDB Dedicated clusters. You can learn more in our VPC peering documentation and AWS PrivateLink documentation and sign up here to get started. And if you have any questions, feel free to swing by our community Slack Channel.
We recently announced that CockroachDB Dedicated is PCI-DSS compliant so it is certifiably safe to store confidential data. Which opens up more workloads that can be run on the fully managed service. We can’t wait to see what you build!