The rate of ransomware attacks is increasing. Year over year, the number of publicly mentioned victims of these attacks have reached historic highs, including one report mentioning a 126% year-over-year increase. High-profile organizations across industries have fallen victim to such attacks, leading to substantial operational disruptions. Few, if any sectors are safe from ransomware attacks:
Healthcare: DaVita Inc., a major U.S. dialysis provider, experienced a ransomware attack that encrypted parts of its network, disrupting operations (Reuters, April 14, 2025).
Finance: Singapore's DBS Group and Bank of China's Singapore branch faced potential data exposure after a ransomware attack on their data vendor (Reuters, April 7, 2025).
Energy: ENGlobal Corporation, a major energy industry contractor, was locked out of some systems for six weeks due to a ransomware attack (CM Alliance, February 3, 2025).
In this ever evolving landscape, where the rate and complexity of attacks is evolving at an increased pace, CockroachDB, the enterprise-ready distributed SQL database, offers architectural resilience and built-in disaster recovery features that can help organizations withstand and recover from ransomware attacks.
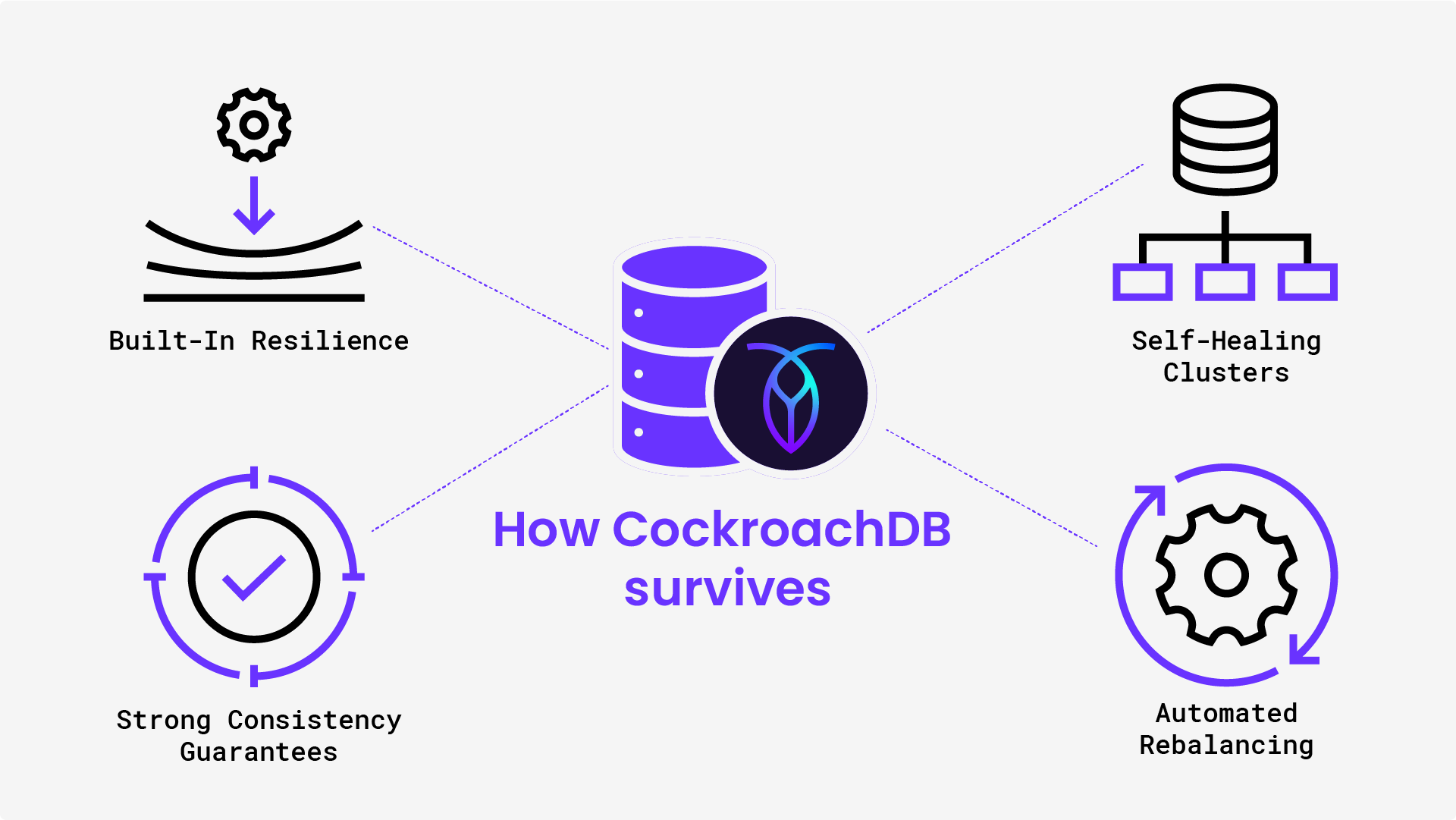
CockroachDB’s Technical Capabilities for Ransomware Resilience
Modern ransomware defenses require more than perimeter security. Infrastructure needs to be inherently resilient. CockroachDB is engineered with this philosophy in mind, offering a set of architectural and operational features that help organizations withstand, contain, and rapidly recover from ransomware attacks. From distributed replication and immutable data storage to point-in-time recovery (PITR), encryption, and full-cluster replication, CockroachDB provides layered protection designed to preserve data integrity, limit blast radius, and ensure business continuity even under active threat.
Distributed, Replicated Architecture
CockroachDB's architecture automatically replicates data across multiple nodes and locations. This means that even if a ransomware attack compromises one node, the data remains accessible and intact on other nodes. The impact node can be removed and replaced, eliminating the risk of additional attack from that machine.
Point-in-Time Recovery (PITR)
When using backups configured with ‘WITH revision history’, PITR allows organizations to restore the database to a specific moment before the ransomware attack occurred. This minimizes data loss and downtime, enabling swift recovery.)
Immutable Multi-Version Concurrency Control (MVCC)
MVCC ensures that data is never overwritten in place, preserving a history of operations. This feature aids in tracing malicious activities and restoring data to a known good state.
Encrypted Data at Rest and in Transit
CockroachDB employs encryption for data both at rest and in transit, safeguarding against unauthorized access and data breaches.
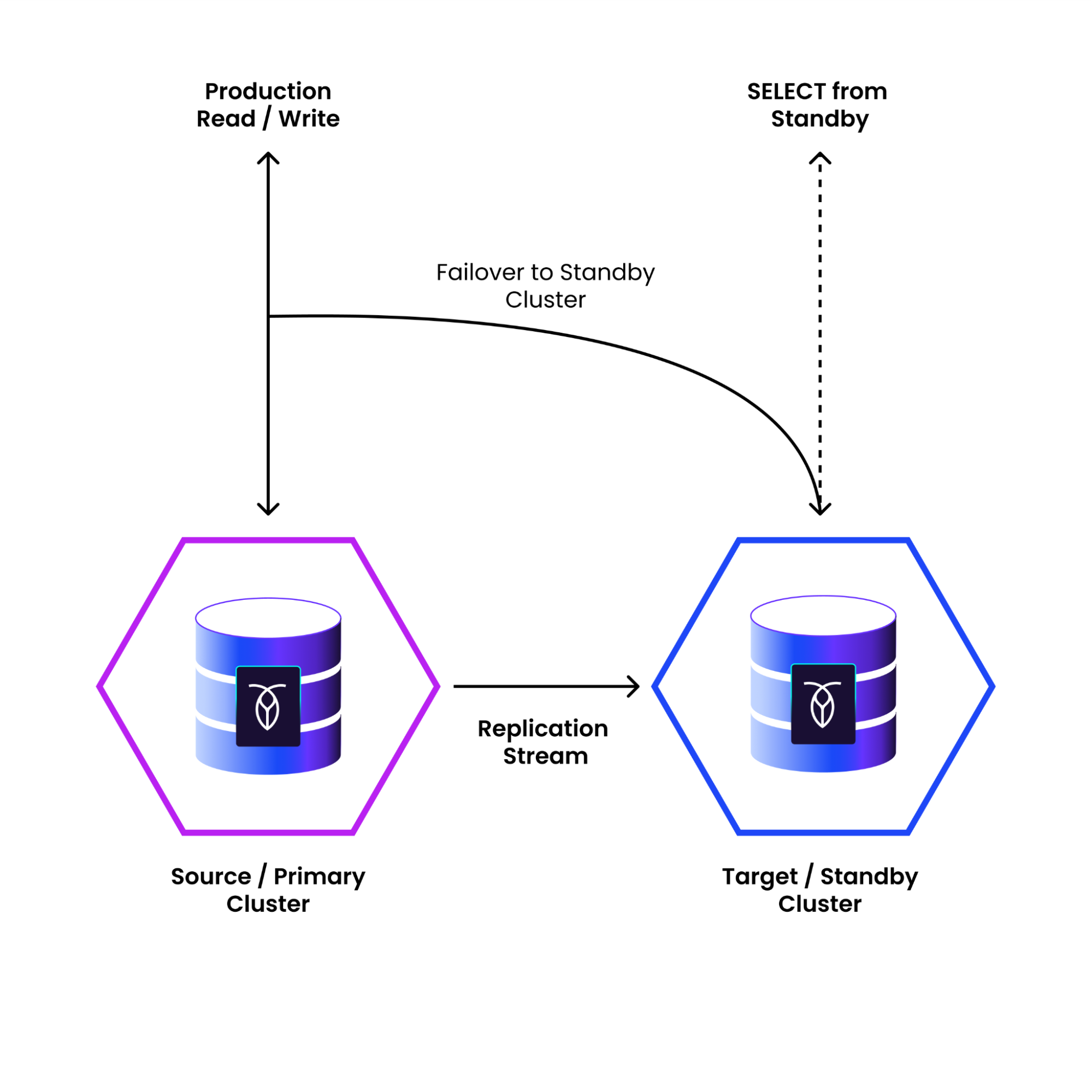
Physical Cluster Replication (PCR)
Physical Cluster Replication maintains a continuously updated, isolated physical copy of the entire cluster, enabling rapid failover and clean recovery if ransomware compromises the primary environment.
Recovery Scenarios with CockroachDB
Regardless of how an organization deploys CockroachDB, restoring operations after a ransomware incident is made easier with CockroachDB’s built-in resilience features. Below are some, but not all, of the practical steps and capabilities that assist in ensuring data integrity, minimizing downtime, and supporting a clean, controlled return to normal operations when deploying in self-hosted environments and additional features Cockroach Labs can provide if deploying within CockroachDB Cloud.
Self-Hosted Environment
Isolation: Infected nodes can be isolated, preventing further spread.
Restoration: Utilize Point In Time Recovery (PITR) and healthy replicas to restore data to a known good state from prior to any identified attack.
Backup Validation: can provide confidence that your backup is restorable and correct.
Verification: Data Integrity is ensured through multi-nodal deployment, allowing infected nodes to be removed and replaced as seamlessly as possible.
Integration with Security Tools: CockroachDB's logs and metrics can be integrated into Security Information and Event Management (SIEM) systems, enabling early detection and automated alerts for potential threats.
CockroachDB Cloud
Managed Recovery: Cockroach Labs provides support for automated recovery processes.
Automated Backups: Regular snapshots and PITR (via As Of System Time queries) facilitate seamless rollbacks.
Immutable Backups: Customers can, outside of the Cockroach managed environment, create and schedule remote, immutable backup targets, adding an additional layer of security in depth.
Continuous Monitoring: Cockroach Labs ingests, monitors, and alerts on all changes and activity relating to customer clusters. Additionally, runtime monitoring is available as part of the Advanced Security Feature available on the platform.
Operational Efficiency: Reduces the burden on internal teams during recovery efforts.
Conclusion
Ransomware attacks are an ever-present risk. CockroachDB’s resilient architecture and comprehensive recovery features offer organizations the ability to withstand disruption and maintain business continuity during and after such an attack. By building on CockroachDB, companies can recover quickly from attacks while strengthening their infrastructure against future threats. If you’re looking to elevate your ransomware resilience strategy, our team at Cockroach Labs would love to talk!
For more information on CockroachDB's disaster recovery features, visit the overview in our docs.
Try CockroachDB Today
Spin up your first CockroachDB Cloud cluster in minutes. Start with $400 in free credits. Or get a free 30-day trial of CockroachDB Enterprise on self-hosted environments.
Mike Geehan is Head of Security for Cockroach Labs.